FREE OFFER: Enterprise Wide Log4j/Log4Shell and Other Vulnerabilities Detection.
FREE OFFER: Enterprise Wide Log4j/Log4Shell and Other Vulnerabilities Detection.
In view of the pervasive and devastating effect of the Log4j vulnerabilities ( actually we’ve now seen multiple iterations of this vulnerability), we’re offering a NO OBLIGATION, NO COMMITMENT evaluation for interested organizations as it relates to discovering these vulnerabilities across their entire IP Address space, i.e. the scope of RFC 1918. As at today, 20th December, 2021, no other vendor or platform offer the scope and coverage our platform- NodeZero Autonomous Penetration Platform.
The platform takes less than 10mins (TEN MINUTES) to set up. Find below an overview of the proposed solution we’re leveraging for this offering. You can also find highly informative and educative resources on how the NodeZero platform addresses the Log4j / Log4Shell vulnerabilities, https://www.horizon3.ai/use-cases/log4shell/
NodeZero Overview.
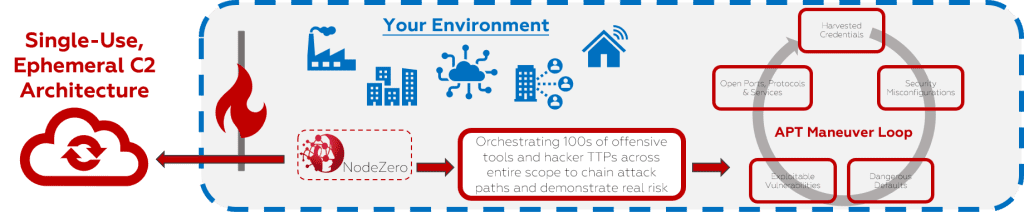
NodeZero is a fully-automated cyber attacker that emulates the tools, tactics, and techniques of real-world attackers, so you can find and fix what matters NOW!
No Pervasive or Persistent Agents … 1-Click User Experience … Safe to Run in Production.
This is true SaaS. NodeZero is an unauthenticated and ephemeral container you spin up and use on a Docker host. From a single machine anywhere in your environment, NodeZero examines and exploits your enterprise, recording a path to your critical assets, identifying vulnerabilities, chaining weaknesses and earmarking precious data. NodeZero validates what it thinks an attacker can do and delivers those results to you.
At a deeper technical level….
NodeZero enumerates and exploits benignly…learning about each host and the environment and making connections
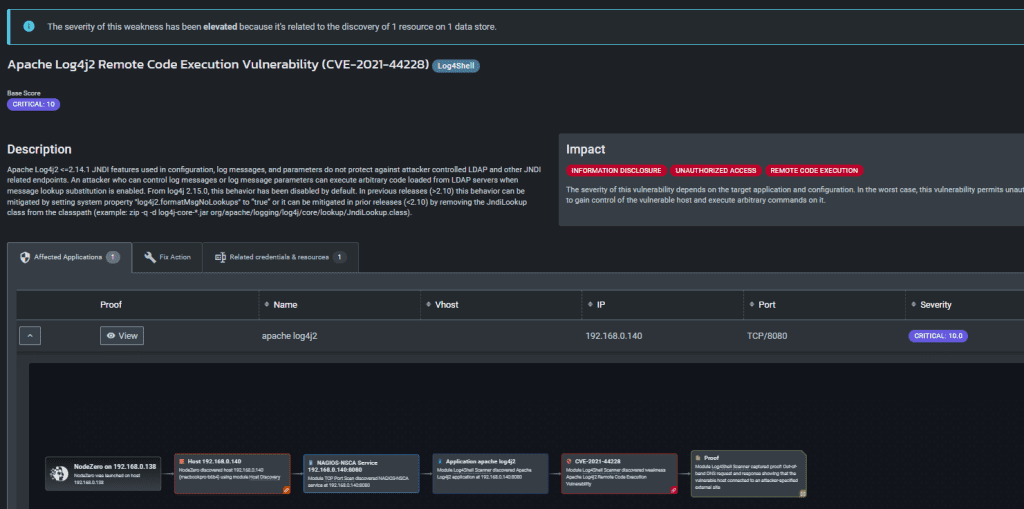
· Host includes port, service, and application discovery; then fingerprint applications to determine specific versions and attempt benign exploitation, and if successful capture proof of exploitation. NOTE: NodeZero attempts to and distinguishes between successful exploitation vs not, I.E., no false positives and un-exploitable vulnerabilities
· Domain enumeration includes DNS, Active Directory pilfering, etc., then attempt to obtain usernames, credentials, and insecure policies to further exploit
· Web enumeration includes virtual host discovery, endpoint discovery, and using machine learning to identify web pages of interest with high value for other attack methods to take advantage of
· Cloud enumeration expands to include cloud-native capabilities, such as infrastructure as code, exposed data buckets, default credentials, and queuing structures to further exploit
NodeZero then communicates all information feeds back into our algorithms to enable targeted post-exploitation, including access to different critical data resources and credentials
Is NodeZero safe?
NodeZero is safe to run in your production environment. It uses benign exploitation techniques to validate weaknesses, gather proof, and reduce false positives without disrupting your systems and services.
· We do NOT store the contents of any sensitive data we locate.
· We do NOT store full passwords, only first & last letter.
· We do store minimal host/service/weakness fingerprints (name, IP, port, etc) for reporting and algorithm tuning purposes.
Bottom Line: NodeZero chains multiple weaknesses, credentials, services, and misconfigurations to create a bread crumb trail and surfaces the attack path with proof of exploit without disrupting your systems.
I’m available for a detailed presentation of this platform. Additional information at www.smsam.net/blog