Autonomous Penetration Testing
Discover and exploit weaknesses in your network just as an attacker would
Reveal Critical Impacts

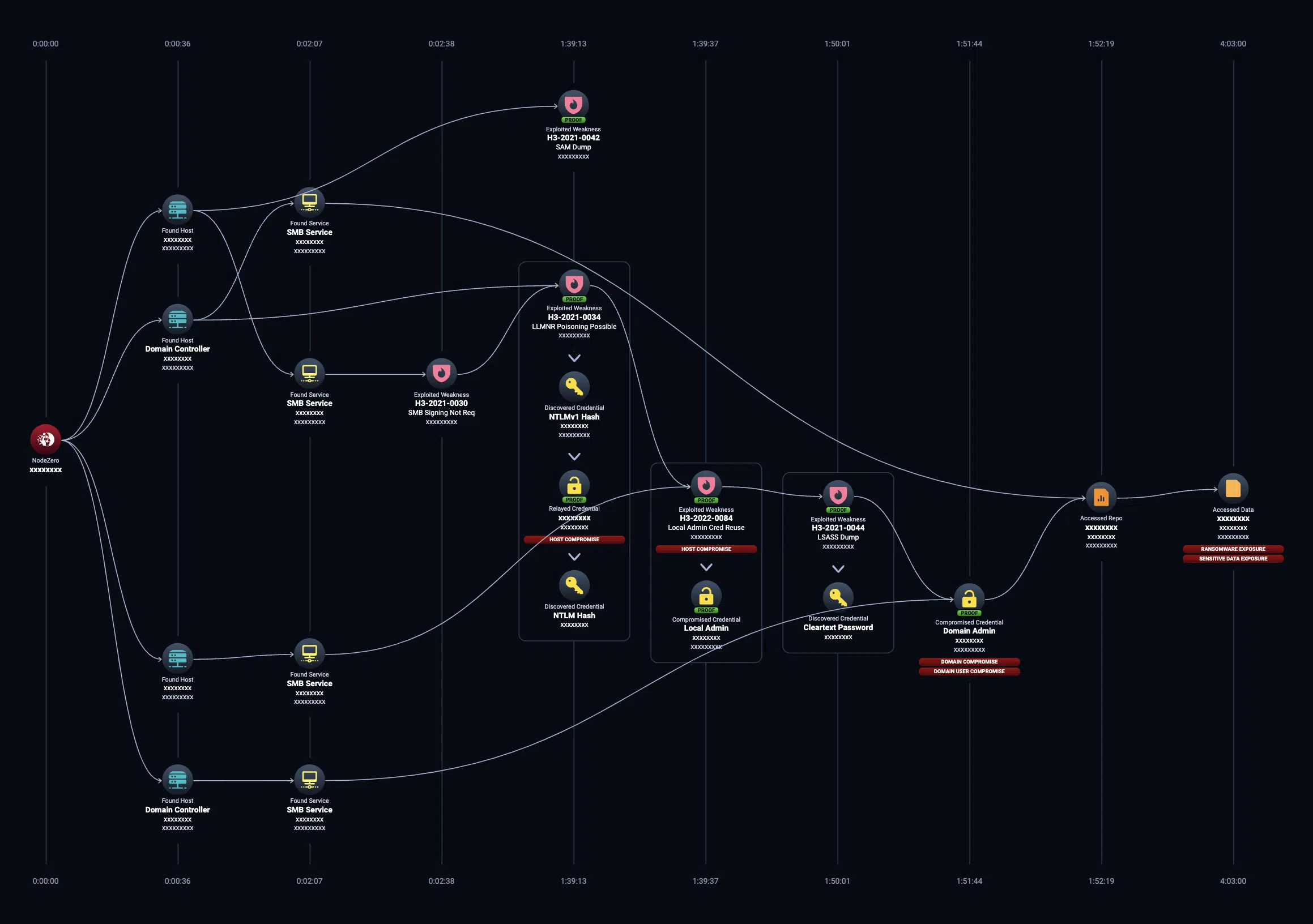
Our Autonomous Pentets Software orchestrates hundreds of offensive security tools and chains weaknesses together to demonstrate the types of impacts attackers seek:
- Domain compromise
- Business email compromise
- Access to sensitive data exposure
- Ransomware
- Ability to pivot to the cloud
- And more!
Improve Security, Prevent Ransomware, Ensure Compliance
Validate and improve your security posture, proactively protect against ransomware, and streamline your compliance initiatives.
