Network threat detection using Flow analytics (NetFlow, IPFIX, sFlow and jFlow ) is a valuable enhancement to network monitoring. So then, implementing a SIEM platform that has native integration with all types of flows takes network security to the next level, combining the ultimate threat detection solution with the in-built SIEM capabilities. Isn’t a SIEM Enough? […]
Five Critical Questions To Ask Microsoft Regarding Identity /Users Credentials Security.
Five Critical Questions To Ask Microsoft Regarding Identity /Users Credentials Security. Folks, I would like to share a thought that I consider as the most important as it relates to securing your organization’s IT assets across On-Premises and Cloud infrastructures against devastating cyber-attacks and malicious insiders breaches. I’ll recommend you all keep an OPEN MIND while reading […]
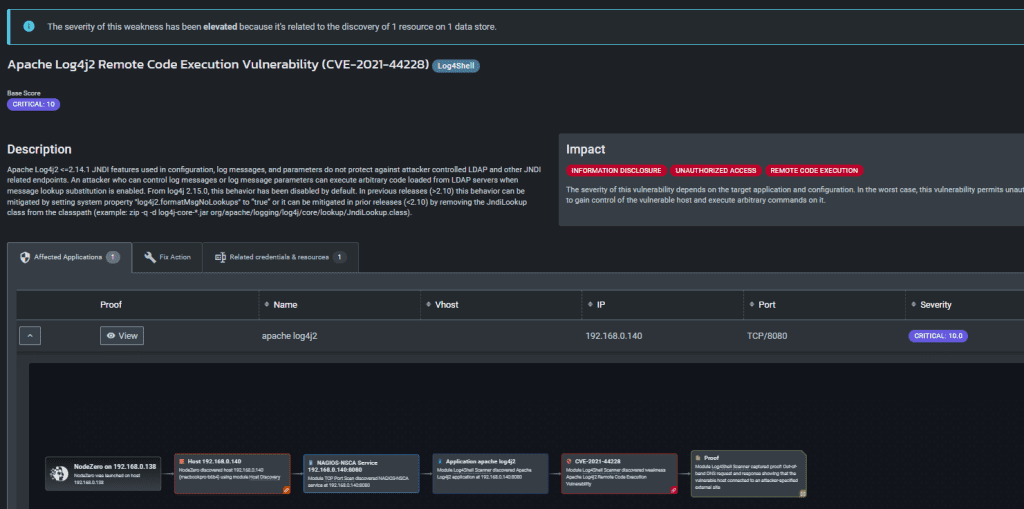
FREE OFFER: Enterprise Wide Log4j/Log4Shell and Other Vulnerabilities Detection.
FREE OFFER: Enterprise Wide Log4j/Log4Shell and Other Vulnerabilities Detection. In view of the pervasive and devastating effect of the Log4j vulnerabilities ( actually we’ve now seen multiple iterations of this vulnerability), we’re offering a NO OBLIGATION, NO COMMITMENT evaluation for interested organizations as it relates to discovering these vulnerabilities across their entire IP Address space, i.e. the […]
PRACTICAL CYBERSECURITY In 2022: Staying Miles Ahead of Attackers By Practicing Proactive Cybersecurity Program.
PRACTICAL CYBERSECURITY In 2022: Staying Miles Ahead of Attackers By Practicing Proactive Cybersecurity Program. Vulnerabilities , (including devastating ones) aren’t going away anytime soon, so organization’s ultimate win against the adversaries will be owning a PROACTIVE cybersecurity program giving her an upper hand- with Proofs! Attackers targeting organizations does NOT requires any compliance to security […]
CrowdStrike Identity Protection Platform (Formerly Preempt Security) Capabilities.
CrowdStrike Identity Protection Platform (Formerly Preempt Security) Capabilities. Stopping Ransomware Threats with the CrowdStrike Zero Trust Solution. How To Do Threat Hunting with Falcon Identity Protection. How To Detect and Prevent Lateral Movements with Falcon Identity Protection. How To Detect and Prevent Suspicious Activities with Falcon Identity Protection. How To Enable Identity Segmentation with Falcon […]
Recommended Cybersecurity Solutions for 2022.
Recommended Cybersecurity Solutions for 2022. Based on threat intelligence gathered from the cybersecurity community on the operations of threat actors (hackers) and malicious insiders, organizations should consider updating their cybersecurity program with the following cybersecurity toolsets. 1- Autonomous Penetration Testing. This is a solution that helps organizations to continuously validate their current cybersecurity posture, i.e., […]
Six Key Mistakes Leading to SOC Burnout
Six Key Mistakes Leading to SOC Burnout. If you work in a SOC in any way, this post is highly recommended for you… Mistake #1 – Underestimating the impact the phishing threat has on your SOC Mistake #2 – Thinking you can’t do better than your existing email security provider Mistake #3 – Thinking all […]
Prevent Malicious Emails From Getting Into Users Mailboxes: Comprehensive Security for Office365 (Email, SharePoint, OneDrive & Teams)
Prevent Malicious Emails From Getting Into Users Mailboxes: Comprehensive Security for Office365 (Email, SharePoint, OneDrive & Teams) If your organization is interested in dramatically reducing phishing attacks and other sophisticated email borne attacks down to as much as 92% (with proofs) then read on.. Consider the following. 1- Do you currently deploy Microsoft EOP /ATP […]
Major Mistakes Leading to SOC Burnout and How to Address Them.
Major Mistakes Leading to SOC Burnout and How to Address Them. SOC Members battle with burnout, overload, and chaos. According to Ponemon Institute– “IT security personnel are approaching burnout as they spend increasingly more time on threat investigation while complexity and chaos, alert fatigue and workload grow.” To be more specific about the burnout to […]
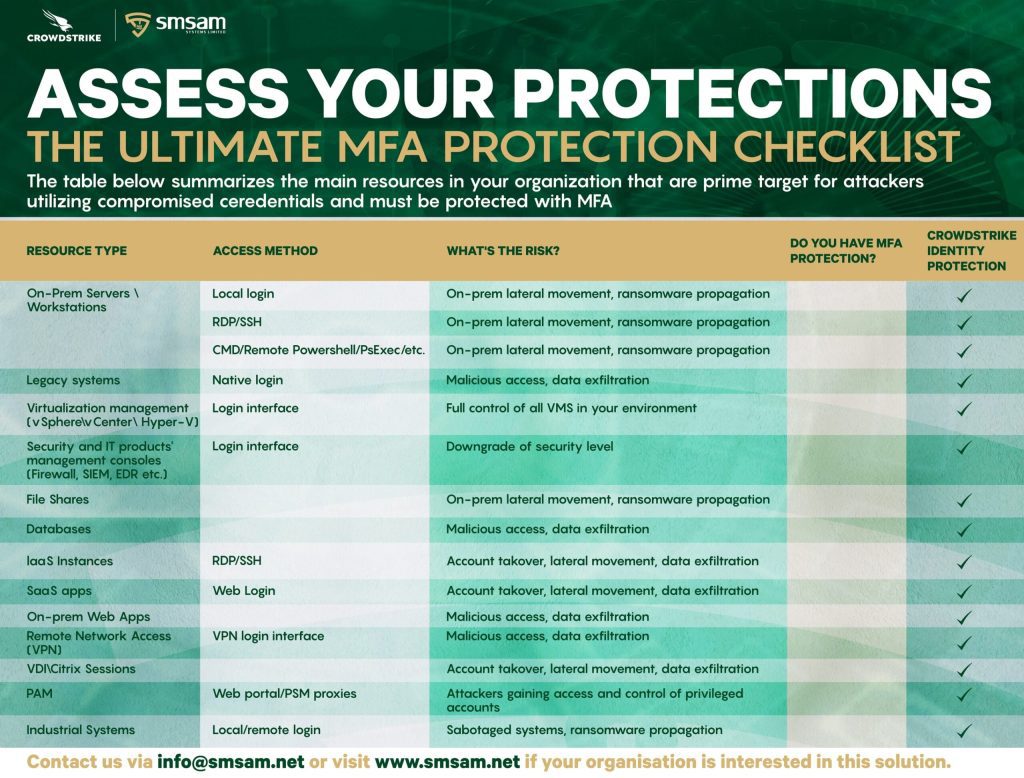
PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud).
PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud). Identity-based attacks that utilize compromised (but valid) credentials to access targeted resources are gaining momentum as the #1 cause of data breaches across both on-prem and cloud resources. Consider the following. 1. Digital Shadows: There are 15B+ Compromised credentials circulate in the dark web, https://lnkd.in/ddVuW_3m […]