Excessive Network Assessment Service
Visualize excessive network access and help implement controls and protect you from unnecessary lateral movement.
How It Works
Discover What Attackers Can
Access in Your Network

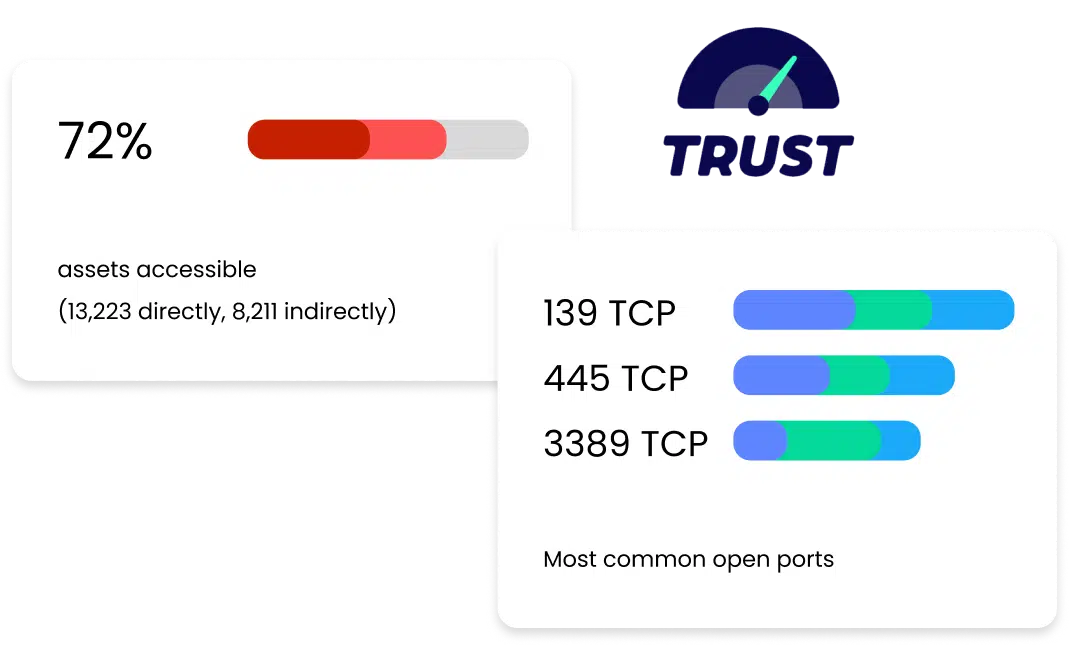
Our Network Assessment Platform collects information from your network via active throttled scanning and pulls identity information from Active Directory, cloud computing services (AWS, Azure, GCP) and other identity providers.
Using this information, We can discover the managed and unmanaged assets in your network, classifying them as clients, servers or cloud hosts
Benefits
Get Detailed Insight Into Your Network Topology
Discover the inner workings of your network with our cybersecurity service. Get a clear picture of its layout, find weaknesses, and strengthen your defenses against cyber threats.
