PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud).
PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud).
Identity-based attacks that utilize compromised (but valid) credentials to access targeted resources are gaining momentum as the #1 cause of data breaches across both on-prem and cloud resources.
Consider the following.
1. Digital Shadows: There are 15B+ Compromised credentials circulate in the dark web, https://lnkd.in/ddVuW_3m
2. Verizon Data Breach Investigative Report: More than 80% of all data breaches involve compromised credentials https://lnkd.in/dJkK7qGh
3. Microsoft: More than 99.9% less likely to be compromised if you use MFA, https://lnkd.in/dGPxq62E
Based on the above, MFA has proven to be the ultimate, practical, and proven solution to block such attacks. This leads to the inevitable conclusion that every resource that is accessed with credentials must be subject to MFA protection.
THE CHALLENGE
Truly comprehensive MFA protection – one that covers all network assets (all workstations, all servers, all LDAP based applications, all protocols, administrative interfaces such as those used in non-interactive logins, etc)- has been exceedingly difficult to achieve, and often isn’t even attempted because it does not seem possible.
THE PROVEN & PRACTICAL SOLUTION.
By integrating with your existing MFA solution and without any form of infrastructures changes whatsoever, the CrowdStrike Identity Protection (Formerly Preempt Security) offers an Improved security posture with extended Extend identity verification/MFA to ANY resource or application, including legacy/proprietary systems and tools that traditionally could not be integrated with MFA — for example, desktops that are not covered by cloud-based MFA solutions, and tools like PowerShell and protocols like RDP over NTLM — to reduce the attack surface.
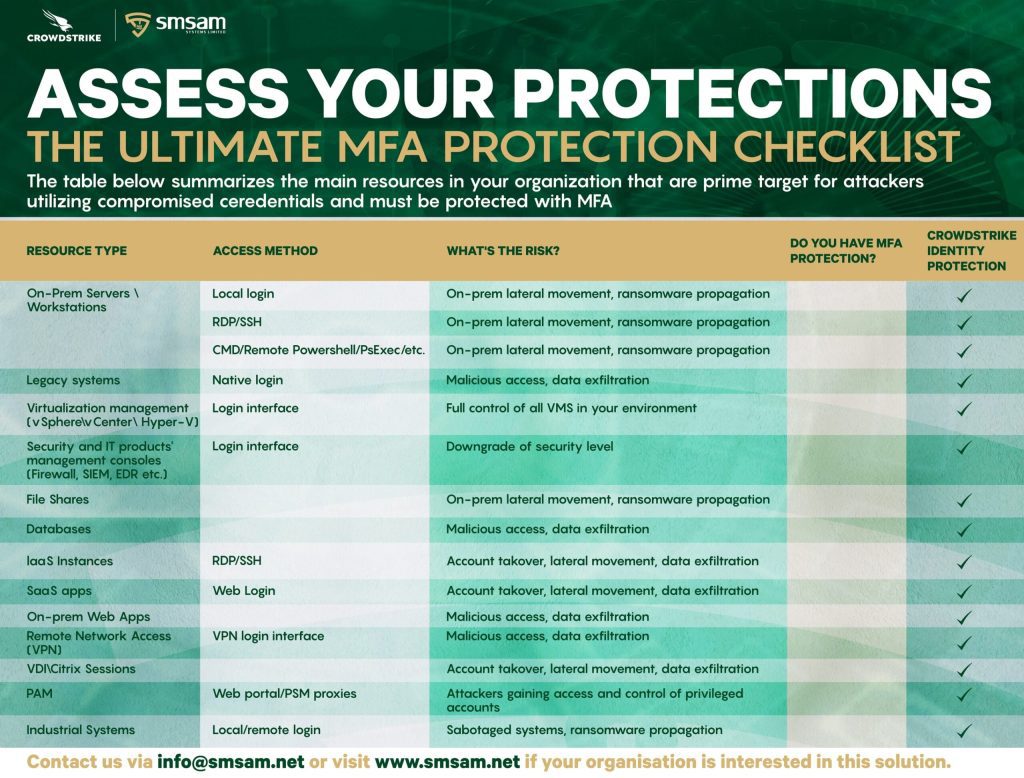
Find attached a one-page document that contained a table which summarizes the main resources in organization that are prime target for attackers utilizing compromised credentials and must be protected with MFA
Join our webinar next week Wednesday for a full demo of how the solution works. Register here https://lnkd.in/d6z5sUB2
