Introducing SMSAM’s Autonomous Penetration Testing Platform. Our autonomous penetration testing platform enables organisations to continuously assess the security posture of their enterprise, including external, identity, on-prem, IoT and cloud attack surfaces. 1- Agentless2-Painless3- Safe to run in production4- Continuous and comprehensive (100% coverage)5- No cheating, scripting, or humans. Additional information here, https://www.smsam.net/services/automated-penetration-testing-as-a-service/
Preventing Ransomware Attacks Through Proactive, Practical, Comprehensive, Continuous and Cost-Effective Cybersecurity Program.
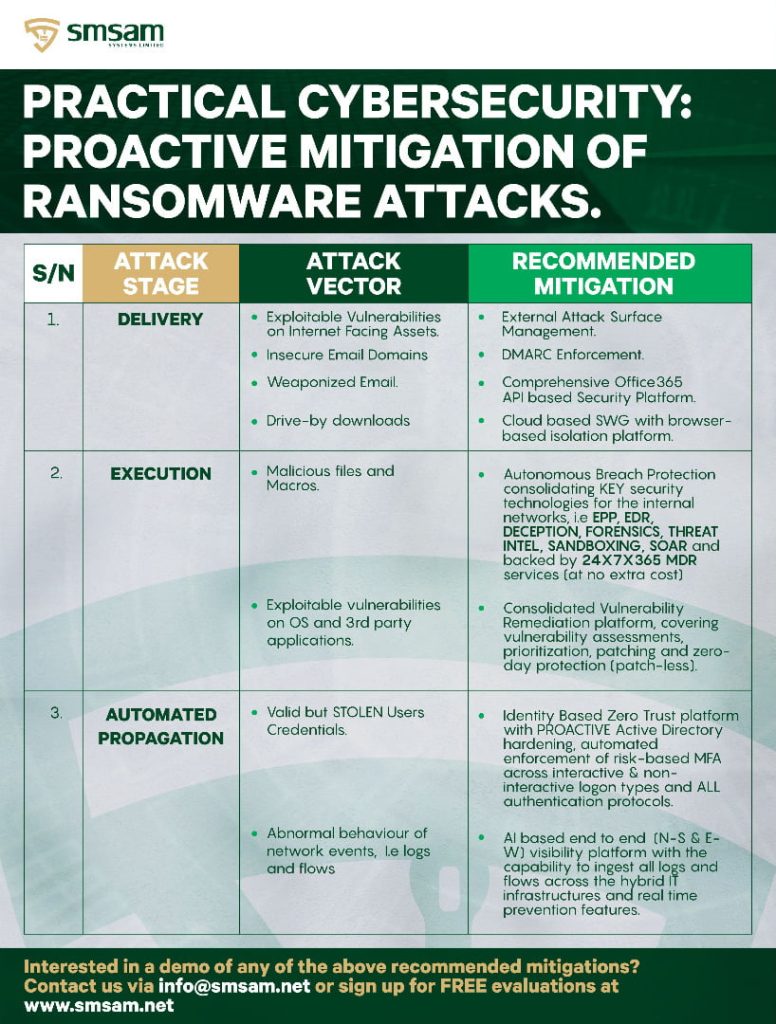
Preventing Ransomware Attacks Through Proactive, Practical, Comprehensive, Continuous and Cost-Effective Cybersecurity Program. The attached image depicts a PROVEN methodical approach that organizations can adopt in combating the devastating effects of ransomware attacks. Again, there are no silver bullets to solving the ransomware attacks pandemic, all that is required is a platform that addresses the basics of cybersecurity […]
Why Your Organization Should Powers its SOC With aiSIEM.
Why Your Organization Should Powers its SOC With aiSIEM. I’d like to share a thought with CISOs, CIOs and Information Security practitioners on how their respective organizations can revolutionize it’s SOC operations by deploying a radically different SIEM platform- aiSIEM. aiSIEM is an advanced analytics, holistic security threat detection and remediation platform that protect all your […]
PRACTICAL CYBERSECURITY: Cybersecurity Management and Awareness Solution For C-Level IT Executives.
PRACTICAL CYBERSECURITY: Cybersecurity Management and Awareness Solution For C-Level IT Executives. I’d like to recommend Continuous Controls Monitoring (CCM) platform to CIOs, CISOs and Senior IT / Cybersecurity practitioners. What is Continuous Controls Monitoring (CCM)? Nearly every cybersecurity practitioner is working to implement and improve their implementation of security controls. Compliance requirements are increasingly putting sharper teeth behind […]
5 REASONS WHY ORGANIZATIONS CHOOSE AVANAN OVER PROOFPOINT, MIMECAST, TRENDMICRO, MESSAGELABS, FORCEPOINT & OTHER ESGs.
5 REASONS WHY ORGANIZATIONS CHOOSE AVANAN OVER PROOFPOINT, MIMECAST, TRENDMICRO, MESSAGELABS, FORCEPOINT & OTHER ESGs. If your organization is interested in a comprehensive, practical and yet cost effective security of the entire Office 365 ecosystems (Email, SharePoint, OneDrive and Teams) then read this…… Avanan Believes in Defense-in-Depth. SEGs Disable Microsoft and Google’s Default Security. Our […]
PRACTICAL CYBERSECURITY: HOW TO STOP INSIDER THREATS WITHOUT LOGS, NO TUNING & AT AN AFFORDABLE COST.
PRACTICAL CYBERSECURITY: HOW TO STOP INSIDER THREATS WITHOUT LOGS, NO TUNING & AT AN AFFORDABLE COST. Think about the following, 1-Why stop short with just detection, when you can prevent attacks that leverage user credentials? 2- Why burden your SOC analysts with questions on false positives, when most of them can be auto resolved by the user? […]
PRACTICAL CYBERSECURITY: Extending MFA Controls to Legacy Applications, Legacy Network Resources & Administrative Tools!
Legacy apps, legacy network resources, legacy authentication protocols, administrative tools, are part of the network and enterprise operations. For example, Mainframe, HR Systems, Powershell, PSexecare too often excluded from Multi-Factor Authentication (MFA) architecture which makes them the weakest link. Remote Desktop Protocol (RDP) use has exploded in use for work from home employees, and DevOps […]
PRACTICAL CYBERSECURITY: Defending Against One Of The Most Sophisticated Vulnerabilities In Any IT Infrastructures.
Vulnerabilities inherent in the NTLM Authentication protocol remains a massive albatross for any Active Directory based Iat infrastructures (about 90% of organizations globally have AD). Most of the sophisticated attacks performed by threat actors leverage NTLM protocol based vulnerabilities and Microsoft has STRUGGLED to get a hand on it! The post referenced here presents one […]
100% AGENTLESS AGENTLESS NETWORK ACCESS CONTROL (NAC) PLATFORM.
Here is an efficient and cost-effective NAC solution for organizations of all sizes. Maintaining regulatory compliance by safeguarding your network doesn’t need to be difficult or expensive.Know and control your network with Easy NAC, the simple and affordable Network Access Control (NAC) solution. Easy NAC automatically discovers devices, profiles them, and controls access to the […]
100% Agentless Network Access Control (NAC) Platform.
100% Agentless Network Access Control (NAC) Platform. A NAC solution that delivers it core capabilities without fuss! See below some of these capabilities. Full visibility of all devices on the network Zero trust, automatic quarantining of rogue devices Alerts to administrators Supports guest access, BYOD, and remediation Collects data from the network Integrates with endpoint […]