CrowdStrike Identity Protection Platform (Formerly Preempt Security) Capabilities. Stopping Ransomware Threats with the CrowdStrike Zero Trust Solution. How To Do Threat Hunting with Falcon Identity Protection. How To Detect and Prevent Lateral Movements with Falcon Identity Protection. How To Detect and Prevent Suspicious Activities with Falcon Identity Protection. How To Enable Identity Segmentation with Falcon […]
PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud).
PRACTICAL CYBERSECURITY: Enforcing MFA Control On ALL Domain Joined Resource ( On-Premises and Cloud). Identity-based attacks that utilize compromised (but valid) credentials to access targeted resources are gaining momentum as the #1 cause of data breaches across both on-prem and cloud resources. Consider the following. 1. Digital Shadows: There are 15B+ Compromised credentials circulate in the dark web, https://lnkd.in/ddVuW_3m […]
PRACTICAL CYBERSECURITY: Extending MFA Controls to Legacy Applications, Legacy Network Resources & Administrative Tools!
Legacy apps, legacy network resources, legacy authentication protocols, administrative tools, are part of the network and enterprise operations. For example, Mainframe, HR Systems, Powershell, PSexecare too often excluded from Multi-Factor Authentication (MFA) architecture which makes them the weakest link. Remote Desktop Protocol (RDP) use has exploded in use for work from home employees, and DevOps […]
Avoiding False Sense of Security With Current MFA Controls.
There are multiple ways that attackers can BYPASS existing MFA controls once they have a foothold in the internal corporate network. 1- Non Interactive Logon. Authentication to resources using SMB, PSExec and other windows native bypasses many MFA controls.2-Degrading Authentication Protocols. Once an attacker is able to degrade the default KERBEROS authentication to NTLM then […]
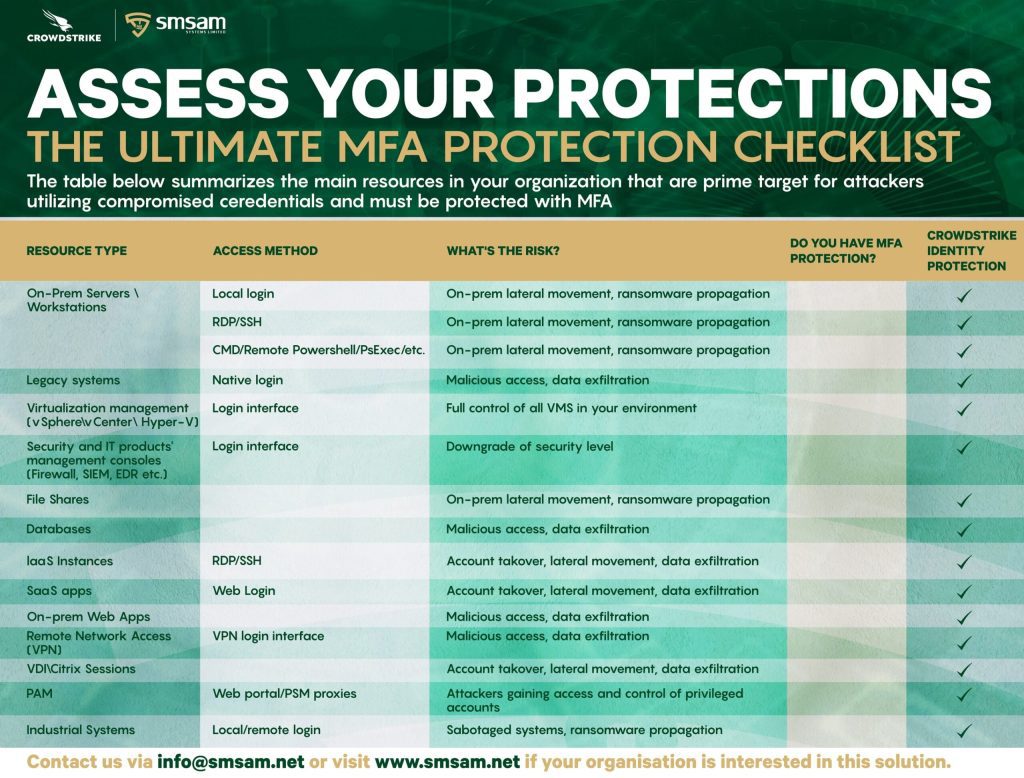
Optimize Your Current MFA Capabilities Across Your Entire Organization IT Infrastructures.
Traditionally, some organizations only leverage MFA mitigations to cover a subset of their IT infrastructures, i.e VPN access, few workstations, servers, and applications. Now, with the out of the box integration with CrowdStrike Falcon Zero Trust (Formerly Preempt Security) the capability of your current MFA (as contained in the attached banner) can be seamlessly extended […]